I did a writeup of the stuxnet story so far for the large german newspaper Frankfurter Allgemeine Zeitung (FAZ), out in print today (now also online here ). Unfortunatelly the page-one teaser image chosen by the frontpage editor is outright silly, and the picture chosen by the FAZ for the main piece is the reactor in Bushehr, as the facility in Natanz is optically less attractive. But, hey, the story is what counts. I want to comment on some of the more detailed aspects here, that were not fit for the more general audience of the FAZ, and also outline my reasoning, why I think stuxnet might have been targeted at the uranium centrifuges in Natanz, instead of Bushehr as guessed by others.

stuxnet is a so far not seen publicly class of nation-state weapons-grade attack software. It is using four different zero-day exploits, two stolen certificates to get proper insertion into the operating system and a really clever multi-stage propagation mechanism, starting with infected USB-sticks, ending with code insertion into Siemens S7 SPS industrial control systems. One of the Zero-Days is a USB-stick exploit named LNK that works seamlessly to infect the computer the stick is put into, regardless of the Windows operating system version – from the fossile Windows 2000 to the most modern and supposedly secure Windows 7.
The stuxnet software is exceptionally well written, it makes very very sure that nothing crashes, no outward signs of the infection can be seen and, above all, it makes pretty sure that its final payload, which manipulates parameters and code in the SPS computer is only executed if it is very certain to be on the right system. In other words: it is extremly targeted and constructed and build to be as side-effect free as humanly possible. Words used by reverse engineers working on the the thing are “After 10 years of reverse-engineering malware daily, I have never ever seen anything that comes even close to this”, and from another “This is what nation states build, if their only other option would be to go to war”.
Industrial control systems, also called SCADA, are very specific for each factory. They consist of many little nodes, measuring temperature, pressure, flow of fluids or gas, they control valves, motors, whatever is needed to keep the often dangerous industrial processes within their safety and effectiveness limits. So both the hardware module configuration and the software are custom made for each factory. For stuxnet they look like an fingerprint. Only if the right configuration is identified, it does more then just spreading itself. This tells us one crucial thing: the attacker knew very precisely the target configuration. He must have had insider support or otherwise access to the software and configuration of the targeted facility.
I will not dive very much into who may be the author of stuxnet. It is clear that it has been a team effort, that a very well trained and financed team with lots of experience was needed, and that the ressources needed to be alocated to buy or find the vulnerabilities and develop them into the kind of exceptional zero-days used in the exploit. This is a game for nation state-sized entities, only two handful of governments and maybe as many very large corporate entities could manage and sustain such an effort to the achievment level needed to build stuxnet. As to whom of the capable candidates if could be: this is a trip into the Wilderness of Mirrors. False hints are most likely placed all over the place, so it does not make much sense to put much time into this exercise for me.
Regarding the target, things are more interesting. There is currently a lot of speculation that the Iranian reactor at Bushehr may have been the target. I seriouly doubt that, as the reactor will for political reasons only go on-line when Russia wants it to go on-line, which they drag on for many years now, to the frustration of Iran. The political calculations behind this game are complex and involve many things like the situation in Iraq, the US withdrawal plans and Russias unwillingness to let the US actually have free military and political bandwith to cause them trouble in their near abroad.
But there is another theory that fits the available date much better: stuxnet may have been targeted at the centrifuges at the uranium enrichment plant in Natanz. The chain of published indications supporting the theory starts with stuxnet itself. According to people working on the stuxnet-analysis, it was meant to stop spreading in January 2009. Given the multi-stage nature of stuxnet, the attacker must have assumed that it has reached its target by then, ready to strike.
On July 17, 2009 WikiLeaks posted a cryptic notice:
Two weeks ago, a source associated with Iran’s nuclear program confidentially told WikiLeaks of a serious, recent, nuclear accident at Natanz. Natanz is the primary location of Iran’s nuclear enrichment program. WikiLeaks had reason to believe the source was credible however contact with this source was lost. WikiLeaks would not normally mention such an incident without additional confirmation, however according to Iranian media and the BBC, today the head of Iran’s Atomic Energy Organization, Gholam Reza Aghazadeh, has resigned under mysterious circumstances. According to these reports, the resignation was tendered around 20 days ago.
A cross-check with the official Iran Students News Agency archives confirmed the resignation of the head of Iran’s Atomic Energy Organization.
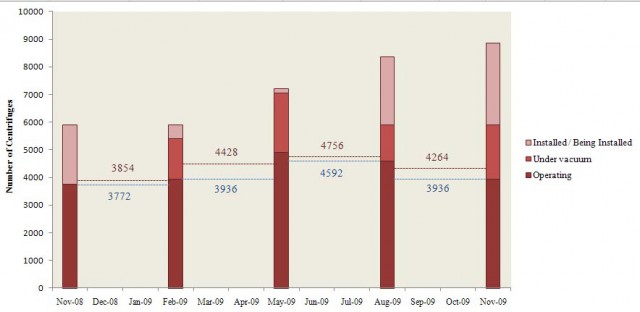
According to official IAEA data, the number of actually operating centrifuges in Natanz shrank around the time of the accident Wikileaks wrote about was reduced substantially .
On 07. July 2009 the israeli news-site ynet-news.com posted a lengthy piece on possibly cyberwar against the Iran nuclear programm. Intriguingly, even contaminated USB-Sticks were mentioned. In retrospect, the piece sounds like an indirect announcement of a covert victory to allies and enemies.
That there are serious anti-proliferation efforts by all available means undertaken by western intelligence is not in doubt. .
There is further indication in the way stuxnet is actually working on the SPS-level. The current state of analysis seems to support the assumption, that the attack was meant to work synchronized and spread over many identical nodes. In a nuclear power plant, there are not many identical SPS-nodes, as there is a wide variety of subsystems of different kind. Compared to this, an enrichment centrifuge plant consists of thousands of identical units, arranged in serial patterns called cascades. Each of them is by necessity the same, as enrichment centrifuges are massively scaled by numbers. stuxnet would have infected each and every one, then triggering subtle of massive failures, depending on the choice of the attacker. To get an impression how the Natanz facility looks from the inside, Iranian President Ahamadinendjad has visited the place in April 2008.
So in summary, my guess is that stuxnet has been targeted at Natanz and that it achieved sucess in reducing the operational enrichment capability sucessfully. We will probably never be able to find out what really happened for sure, unless Iran comes forward with a post-mortem. Stuxnet will go down in history as the first example of a news class of malware, that has been engineered to weapons-grade performance with nearly no side-effects and pinpoint accuracy in delivering its sabotage payload.









